Phishing Campaign Using Morse Code
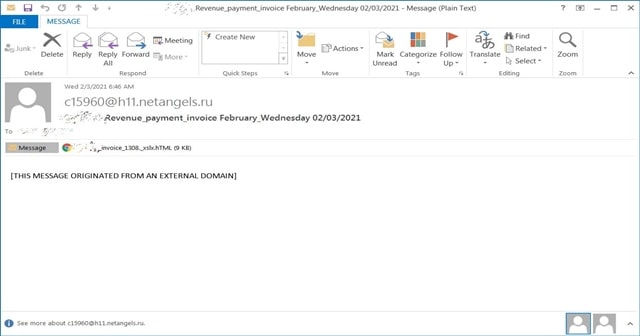
Since the email filtering engines and employees are getting better at detecting general phishing emails, threat actors are developing new methods to find their way in and steal the data. One such novel technique found recently, where the attackers are using More code to hide their scripts. As detailed by BleepingComputer, the campaign was first reported on Reddit and had some of the samples uploaded to VirusTotal last week. Explaining the campaign, it starts with an email bearing the subject as “Revenue_payment_invoice February_Wednesday 02/03/2021.”
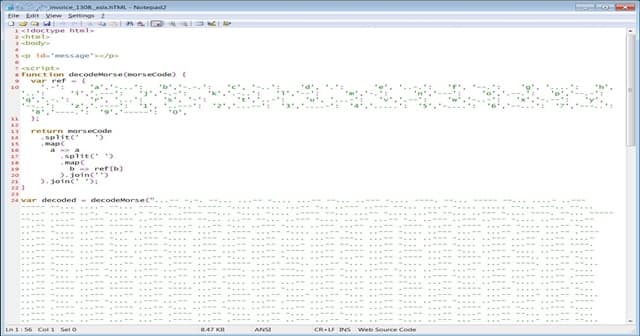
Opening the email will show an attached Excel document titled “[company_name]invoice[number]._xlsx.hTML.” The company name and number will be replaced with the target’s to make it more specific and relatable. Opening the attachment in a text editor shows JavaScript code being written in Morse code.
As the Morse code defines the alphabets and numbers with just dots and dashes, it makes it hard, and unsuspicious to the email filtering engines to detect the malicious links in it. Here, the code is being written in various symbols like ‘a‘ is mapped to ‘.-‘ and the ‘b‘ is mapped to ‘-…‘, etc. Also Read- Best Morse Code Apps For Android A decodeMorse() function was set to decode the string, to finally unpack into JavaScript tags and inject them into the HTML page. These combined will make up a fake Excel page that asks the user (target) to sign-in before viewing. Entering the credentials without realizing it as a fake page will export them to the hacker’s C2. To date, BleepingComputer spotted seven companies targeted with this campaign, namely the SGS, Dimensional, Metrohm, SBI (Mauritius) Ltd, NUOVO IMAIE, Bridgestone, Cargeas, ODDO BHF Asset Management, Dea Capital, Equinti, and Capital Four.